Unveiling the Most Common Types of Cyber Attacks
Unveiling the Most Common Types of Cyber Attacks
Cyberattacks are becoming a more common threat in today's digital environment.
The intensity and sophistication of cyberattacks continue to rise as technology
advances, posing substantial hazards to individuals, corporations, and
governments.
 |
Cyber Security Threats by here |
Let's first define what a
cyberattack is. An attempt to steal, modify, destroy, interfere with, or
disable information resources and systems found in computer networks and
systems is known as a cyberattack. Insider threats and outer threats are the two
types of cyberattacks. Insider threats are perpetrated by individuals who have
lawful access to the systems they target and use that access to intentionally
or unintentionally exploit vulnerabilities. They could be perpetrated by an
employee who is unsatisfied or furious, or by a contractor who has access to
the organization's systems. An outsider threat comes from someone who has no
connection to the system being attacked, such as criminal organizations or
hackers.
 |
| Phishing Attacks by here |
One of the most popular sorts of cyber-attacks is phishing, which involves deceiving people into supplying sensitive information such as usernames, passwords, and credit card information. This is often accomplished through the use of fake emails, SMS messages, or websites that look to be from authentic sources. The attackers frequently utilize social engineering techniques to create a sense of urgency or panic in the victim, prompting them to provide their information.
Identity theft, financial loss,
and unauthorized access to personal or corporate data are all major outcomes of
phishing assaults. To reduce the danger of falling victim to these assaults,
organizations frequently educate their personnel on how to recognize and resist
phishing efforts.
There
are different types of phishing attacks and two of them are also known as,
- Whale Phishing Attacks
A
whale-phishing attack is so called because it targets an organization's
"big fish" or whales, who often include executives in the C-suite or
those in positions of authority. These persons are likely to have useful
information to attackers, such as proprietary information about the business or
its operations. If a targeted "whale" downloads ransomware, they are
more likely to pay the ransom to prevent word of the successful attack from spreading
and harming their or the organization's reputation.
- Spear Phishing Attacks
A spear
phishing assault is a form of targeted phishing attack. The attacker spends
time researching their intended targets before writing statements that the
victim is likely to find personally relevant. Because of the manner the
attacker focuses on a single target, these types of attacks are appropriately
referred to as "spear" phishing. Because the message appears real, it
can be difficult to detect a spear-phishing attempt. A spear-phishing assault
frequently employs email spoofing, in which the information inside the
"From" area of the email is forged, making the email appear to come
from a different sender. This can be someone the target knows and trusts, such
as a member of their social network, a close friend, or a business partner.
Website cloning
may also be used by attackers to make the message appear legitimate. The
attacker clones a real webpage to lure the victim into a false feeling of
security. The target feels safe inputting their personal information because
they believe the website is legitimate.
As a result, we may prevent
phishing assaults from succeeding by being cautious about the emails we open
and the websites we click on. Pay attention to email headers and avoid clicking
on anything that appears dubious. Examine the settings for "Reply-to"
and "Return-path." They must connect to the same domain as specified
in the email.
2. Malware Attacks
 |
| Malware Attacks by here |
Malware, which stands for
malicious software, is a broad category of software that is meant to disrupt,
damage, or gain unauthorized access to computer systems. Malware commonly
includes viruses, worms, Trojans, ransomware, and spyware. Malware attacks can
take many forms, including malicious email attachments, hijacked websites, and
removable storage devices.
When a system becomes infected
with malware, it can result in a variety of bad outcomes, such as data loss,
system corruption, and unauthorized access to sensitive information. Malware
attacks require the installation of software on the target device. This
necessitates the user taking action. As a result, in addition to employing
malware-detection firewalls, users should be informed on which types of
software to avoid, which links to verify before clicking, and which emails and
attachments to avoid.
3. DoS and DDoS Attacks
 |
| Difference between DOS and DDOS by here |
A denial-of-service (DoS) attack
is intended to overload a system's resources to the point where it is unable to
respond to genuine service requests. A distributed denial-of-service (DDoS)
attack is similar in that it attempts to deplete a system's resources. A DDoS
assault is begun by a large number of malware-infected host machines that the
attacker controls. These are known as "denial of service" attacks
because the victim site is unable to serve individuals who try to access it.
A DoS attack floods the target
site with fraudulent requests. Because the site must reply to each request, all
responses utilize the site's resources. This makes it impossible for the site
to serve users normally and frequently ends in the site being completely shut
down.
DoS and DDoS attacks differ from
other sorts of cyber-attacks in that they allow the hacker to gain access to a
system or increase the amount of access they already have. The attacker
directly profits from their efforts in these types of attacks. The goal of DoS
and DDoS network attacks, on the other hand, is simply to disrupt the
effectiveness of the target's service. If the attacker is employed by a
corporate competitor, their efforts may be rewarded monetarily.
A DoS attack can also be used to establish a vulnerability for another form of attack. When a DoS or DDoS attack is effective, the system is frequently forced to go offline, leaving it exposed to other sorts of attacks. Using a firewall to identify whether requests sent to your site are valid is a common approach to avoid DoS attacks. Imposter requests can then be ignored, allowing legitimate traffic to continue uninterrupted. A large internet attack of this type happened in February 2020 against Amazon Web Services (AWS).
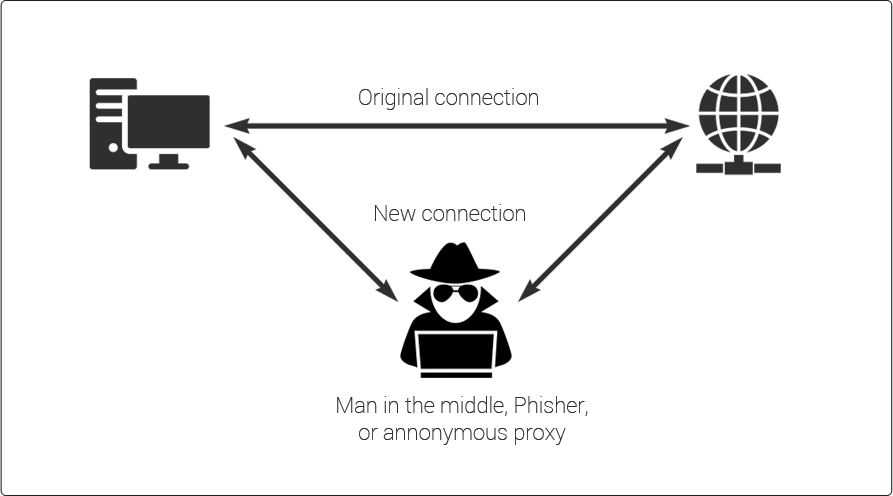
4. Man-in-the-Middle Attacks
 |
| Man-in-the-Middle Attacks by here |
An attacker intercepts
communication between two parties without their knowledge in a
man-in-the-middle (MITM) attack. This enables the attacker to listen in on the
conversation, modify the data being sent, or impersonate one of the parties
involved.
MITM attacks are especially harmful when sensitive information is involved, such as login credentials or financial transactions. Use strong encryption protocols such as SSL/TLS or a virtual private network (VPN) to protect yourself and your organization from MITM attacks.
5. SQL Injection Attacks
 |
| SQL injection attacks by here |
SQL injection attacks
are directed at online applications that employ a database to store and
retrieve information. In order to inject malicious SQL commands into the
database backend, attackers exploit vulnerabilities in the application's input
fields. This can result in unauthorized access to sensitive data, data
modification, or even database penetration.
Developers should use parameterized queries to sanitize user input and avoid malicious SQL injection to prevent SQL injection attacks.
6. Zero-Day Exploits
 |
| Zero-Day Exploits by here |
Zero-day exploits are
software or hardware vulnerabilities that are unknown to the manufacturer and
have not been patched. Before a patch or fix is released, attackers might use
these vulnerabilities to launch targeted attacks.
Zero-day exploits are a serious concern because they can be leveraged to enter systems and networks without being detected. To protect against zero-day exploits, you should be watchful and keep their systems up to speed with the newest security updates.
7. Insider Threats
 |
| Insider Threats by here |
Individuals within an organization
who abuse their access privileges to steal critical information, conduct fraud,
or sabotage systems are examples of insider threats. Insider threats can be
purposeful or unintentional, and they can have major ramifications for the
security and reputation of an organization.
Organizations should create rigorous access controls, monitor user actions, and provide security awareness training to staff to reduce insider risks.
8. Social Engineering Attacks
 |
| Social Engineering Attacks by here |
Social engineering
attacks entail tricking people into disclosing sensitive information or acting
in ways that harm security. Attackers frequently utilize psychological
manipulation strategies to earn their targets' trust and take advantage of
human nature's desire to trust others.
Pretexting, baiting, and tailgating are all examples of social engineering attacks. Organizations should educate their staff about social engineering techniques and put regulations in place to prevent unauthorized access.
9. Advanced Persistent Threats (APTs)
 |
| Advance Persistent Threats (APTs) here |
APTs are sophisticated cyber-attacks carried out by well-funded and organized groups with specific goals. APTs are long-term, targeted attempts to infiltrate a target's network or systems while remaining undiscovered.
APTs frequently entail numerous stages, such as reconnaissance, initial compromise, establishing persistence, lateral movement inside the network, and sensitive data exfiltration. A multi-layered approach to APT defense is required, including enhanced threat detection capabilities and proactive threat hunting.
10. DNS Spoofing
 |
| DNS Spoofing by here |
A hacker uses Domain
Name System (DNS) spoofing to redirect traffic to a bogus or "spoofed"
website. Once on the fake site, the victim may enter important information that
the hacker may use or sell. The hacker may also create a low-quality website
with disparaging or provocative information in order to make a competitor look
bad.
The attacker uses DNS
spoofing to take advantage of the fact that the victim believes the site they
are visiting is real. From the perspective of the visitor, this allows the
attacker to commit crimes in the name of a legitimate firm.
To prevent DNS
spoofing, keep your DNS servers up to date. Attackers target DNS servers for
weaknesses, while the latest software versions frequently include solutions
that close known flaws.
11. Trojan Horse
 |
| Trojan Horse by here |
A Trojan horse assault
employs a harmful program concealed within a seemingly normal one. When the
user runs the seemingly harmless program, the virus inside the Trojan can be
used to open a backdoor into the system, allowing hackers to infiltrate the
computer or network. The myth of the Greek troops who hid inside a horse to
invade the city of Troy and win the war inspired the name of this menace. The
Greek warriors jumped out and attacked after the "gift" was accepted
and brought within the gates of Troy. Similarly, an ignorant user may accept an
innocent-looking application into their system, only to discover it contains a
concealed hazard.
Users should be instructed not to download or install anything unless the source can be confirmed to avoid Trojan attacks. NGFWs can also be used to inspect data packets for potential Trojan threats.
12. URL Interpretation
Attackers employ URL
interpretation to alter and fake certain URL addresses in order to get access
to the target's personal and professional data. This type of attack is also
known as URL poisoning. The term "URL interpretation" refers to the
attacker's knowledge of the order in which the URL information for a web page
must be input. The attacker then "interprets" this syntax, figuring
out how to gain access to regions they do not have access to.
A URL interpretation
attack involves a hacker guessing URLs that can be used to get administrator rights
on a site or access the site's back end to gain access to a user's account.
Once on the desired page, they can alter the site or acquire access to
sensitive information about others who use it.
Use secure
authentication techniques for any critical portions of your site to prevent URL
interpretation attacks from succeeding. Multi-factor authentication (MFA) or
safe passwords made up of seemingly random characters may be required.
How to prevent Cyber Attacks:
 |
| Preventing Cyber Attacks here |
Fighting cyber-attacks
requires a multifaceted strategy that includes prevention, detection, and
response. Here are some approaches to common forms of cyber-attacks:
- · Update your software.
- · Install a firewall.
- · Back up data.
- · Encrypt data.
- · Use strong passwords.
Cyber-attacks take many forms and
continue to pose serious threats to individuals, corporations, and governments.
Understanding the various forms of cyber-attacks is critical for developing
effective security measures and limiting risks. To guard against growing cyber
threats, organizations should prioritize cybersecurity knowledge and invest in
solid security solutions.
Comments
Post a Comment